
The outcomes we deliver clients are validated breaches that are investigated, contained and remediated.
All incidents are aligned to the kill chain and Mitre ATT&CK frameworks and contain detailed investigative actions and recommendations that your organisation follows to protect against the unknown, insider threat and malicious attacker.
As your partner, we can become an extension of your internal team by augmenting your MSSP, or be a full-service SOC as a service security solution.
Recon
Look outside your network to find evidence of a breach or one that might be in works. Our proprietary technology and know-how monitor the deep and dark web for you.
Detect
Catch known and unknown threats that bypass perimeter controls with a virtual sensor delivering integrated, multi-layer detect-in-depth capability.
Deceive
We weave a layer of illusion over your network, covering every endpoint, server and identity with deceptions.
Hunt
High performance threat hunting and incident response augmented by behaviour and analytics technology.
Respond
Quickly identify, quarantine and block threats with unintrusive sensors that utilise behavioural monitoring and machine learning in conjunction with our analysts.
Intelligence
Tap the power of community to protect you, with over 100 threat intelligence sources that correlate directly to your real-time network logs.
LMNTRIX FOR IoT/OT
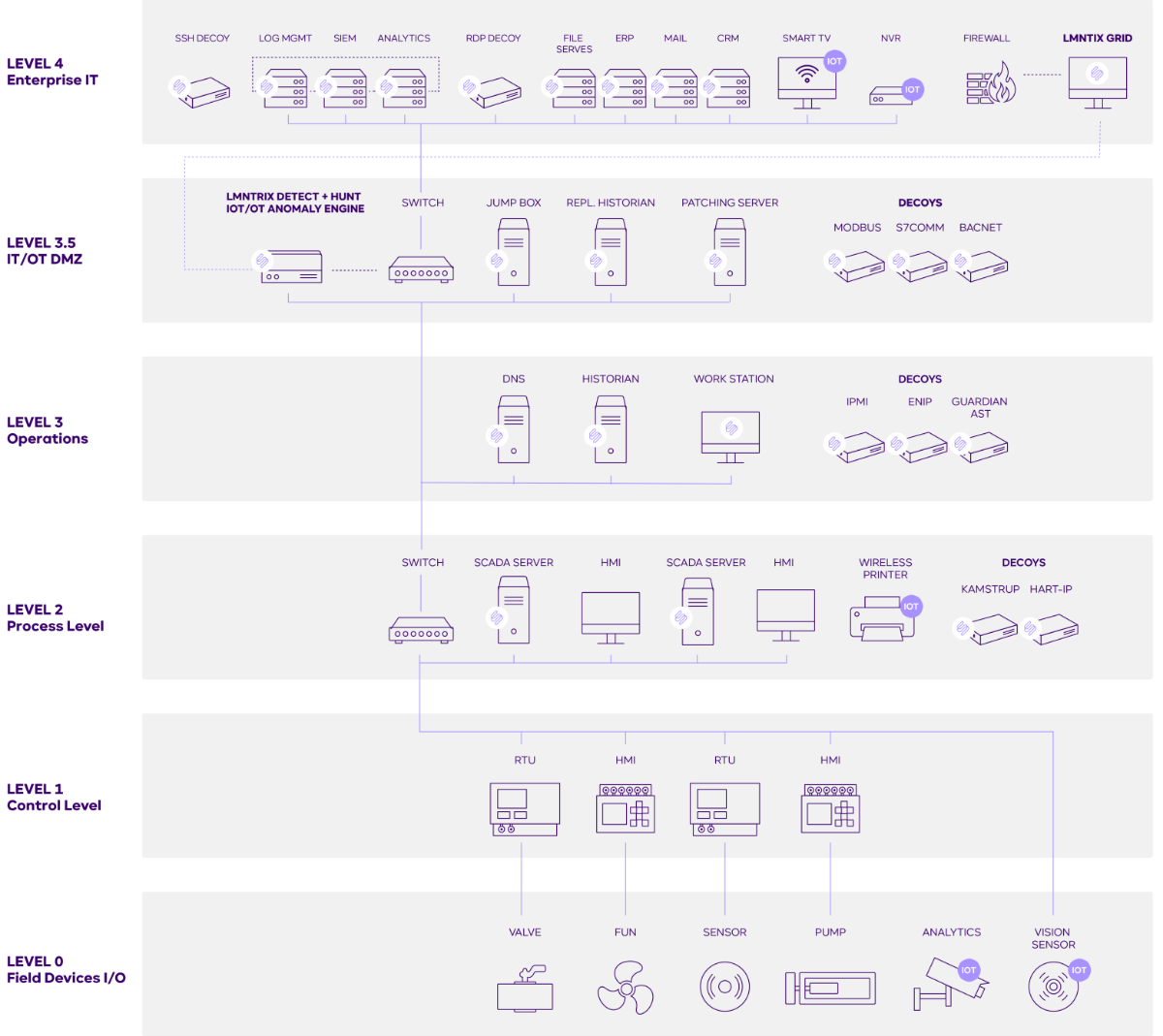
The LMNTRIX architecture and technology stack provides complete support for ICS/SCADA environments.
The LMNTRIX multi-vector and holistic architecture detects any threat to the SCADA application, process or network, providing granular visibility of SCADA traffic and facilitating attack forensics:
We monitor and record all SCADA activity out-of-band and independent of the ability of SCADA devices to send logs.

We baseline normal behaviour and alert on deviations from the baseline to prevent undesired network operations based upon policy.

Weave a layer of illusion over your network, covering every endpoint, server and identity with deceptions

All security and events related to our architecture are centrally managed, providing a complete view across your enterprise and control networks.

We support the industry’s most extensive support of ICS/SCADA-specific protocols including BACNet, DNP3, IEC-60870-5-104, IEC 60870-6 (ICCP), IEC 61850, MMS, Modbus, OPC, Profinet, S7 (Siemens) and many others.

We detect and prevent exploits of ICS vulnerabilities with SCADA IDS signatures and on the endpoint using exploit prevention using hardware assisted control flow integrity (HA-CFI), closing the window of exposure between vulnerable and patched systems.

We detect lateral movement using SCADA specific deceptions.

Our platform is fully managed and is completely operationalized by the LMNTRIX Cyber Defense Centers and includes 24/7 Analyst Driven – Continuous Monitoring, Hunting & Response.
The following diagram shows a typical deployment of our solution on Enterprise networks.
Secolve XDR
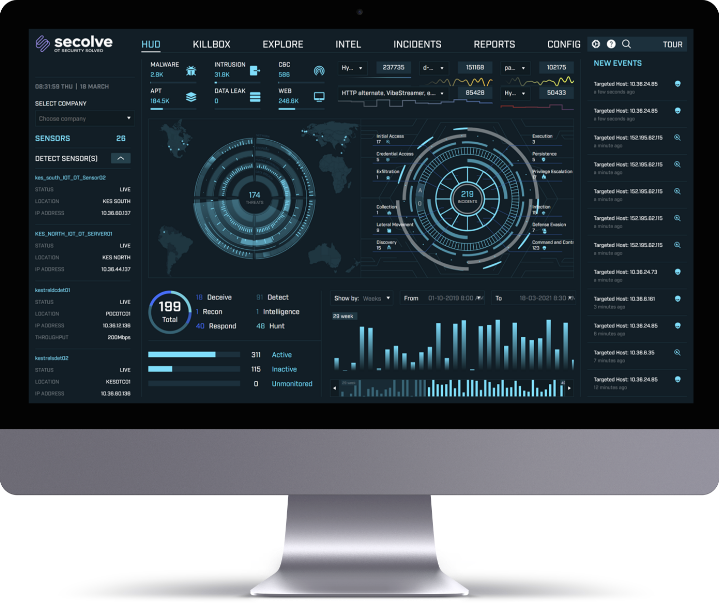
Backed by a 24/7 Managed Detection and Response service – at no extra cost – Secolve provides comprehensive protection of the environment for even the smallest security teams. It is a single investigative platform for insights into threats on enterprise, cloud, hybrid, and industrial control systems (ICS) networks.
The Secolve XDR delivers unique advantages over current network security solutions. It is a holistic and multi-vector platform with unlimited retention window of full-fidelity network traffic, innovative security visualizations, and the ease and cost-savings of an on-demand deployment model.
Don’t be challenged by growth and digital transformation.
Let Secolve provide your organisation with practical security solutions
to enhance your OT/ICS operations.
 24×7 OT Platform
24×7 OT Platform